Rambles by Stephen Shaw
Unlistable Basic Programs and fixing them
Did you ever want to make an Extended Basic program unlistable and unalterable but still playable and saveable?` This is a bit of fun programming to see how to exploit the way our computer stores its programs.Original programs from Tidewater Newsletter, Ken Woodcock - I took them from WORDPLAY June 1990:
Your computer stores all the basic program lines in one block; and then in a separate block, a line number table, which identifies where in memory each line number can be found- the line number table is in numeric order, the actual program lines are stored in the order you enter them, which may not be in numeric order!
To make a program unlistable all you need do is change all the length bytes in the LNT! The following program will set all length bytes to zero and requires XB and 32k ram.
First load your program. If it uses lines 1 and 2, resequence it!
Then MERGE in (or type in) the following code:
1 CALL. INIT :: CALL PEEK(-31952,A,B,C,D) :: SL=C*256+D-65539 :: EL=A*256+B-65536 :: FOR X=SL TO EL STEP -4 :: CAL
L PEEK(X,E,F,G,H) :: ADD=G*256+H-65536 :: PRINT E*256+F
2 CALL LOAD(ADD-1,0) :: NEXT X :: STOP :: !@P-
[ TISHUG has a slightly modified format of this listing as follows:
1 CALL INIT :: CALL PEEK(-31952,A,B,C,D) :: SL=C*256+D-65539 :: EL=A*256+B-65536 :: FOR X=SL TO EL STEP -4 :: CA
LL PEEK(X+2,G,H) :: CALL LOAD(G*256+H-65537,0) :: NEXT X ]
What is it doing?
First PEEK four bytes from -31952 for the top and bottom addresses of the line number table. (Line 1, obtain SL and EL).
Then step through these -four bytes at a time- the first two bytes (E,F) are the line number, then the next two which we are going to use (G,H) are the address at which the program line starts. We look at the address where the program line starts LESS ONE (-65537 instead of -65536) because this initial byte is the actual line length. It is NOT used to execute a line, which is in tokenised form, but it is required when we LIST a program as the tokens have to be “undone" and it is easier to put a length indicator in than install a more intelligent untokeniser.
The first byte of the memory address which the Number Table points to tells the computer how long the line is in bytes- this is only used to list the program or to handle editing functions. When a program is running, a zero value byte terminates each program line and the LNT is only used to locate the start of the program line. So we are able to make a program unlistable and uneditable without preventing it running!
Now RUN the amended program.
Now in command mode type in 1 [enter], 2 [enter] to remove the extra lines.
Now save using a different file name if to disk or a different tape if to cassette!!!
And you can now RUN the program, no trouble- try it. BUT... what happens if you try typing EDIT 100 or LIST
What... you saved the amended program over your original? Not to worry you can get it back.
We could alter all the length bytes to the maximum possible, which would certainly allow the program to be LISTed again (change the value 0 in line 2 above to 255),
1 CALL INIT :: CALL PEEK(-31952,A,B,C,D) :: SL=C*256+D-65539 :: EL=A*256+B-65536 :: FOR X=SL TO EL STEP -4 :: CALL PEEK(X+2,G,H) :: CALL LOAD(G*256+H-65537,255) :: NEXT X
but editing could still be problematical, so lets reset the length bytes to what they should be!
Looking for a zero byte is a start, but not the end, as a zero byte may also occur in certain cases in the program line. The simplest thing to do is to look for a zero byte, then look at the line number table to see if the value obtained is an actual start of a program line. So lets do it...
First load the corrupted program- you cannot list it to see if it uses lines 1 to 6, so RESequence it for safety! then MERGE in the following lines:
1 CALL INIT :: CALL PEEK(-31952,A,B,C,D) :: SL=C*256+D-65539 :: EL=A*256+B-65536 :: FOR X=SL TO EL STEP -4 :: CALL PEEK(X,E,F,G,H) :: ADD=G*256+H-65536 :: PRINT E*256+F
2 I=1 :: CALL PEEK(ADD-1,V) :: IF V THEN 6
3 CALL PEEK(ADD+I,V,W) :: IF V THEN I=I+1 :: GOTO 3
4 FOR Y= SL TO EL STEP -4 :: CALL PEEK(Y,E,E,E,F) :: IF E*256+F-65536=ADD+I+2 OR =0 OR ADD+I>-3 THEN CALL LOAD(ADD-1,I+1):: GO TO 6
5 NEXT Y :: I=I+1 :: GOTO 3
6 NEXT X :: STOP :: !@P-
Some of those lines are a little long by the way- when your console honks at you to Say it won't take any more characters THANK YOU, you press ENTER, then bring the line back with EDIT N or N (FCTN X), move the cursor to the end of the line and carry on typing.
Run this amended program- it takes a little longer this time!!! and when it has finished your program is uncorrupted, lines 1 to 6 can be removed and the program saved, listable and editable.
Too slow? From an anonymous author, a machine code fix! This comes from the Sydney News Digest of July 1990 and requires assembly WITHOUT the C option:
* This program re-enters the
* line length values within
* a Basic program.
*
* For use when a program is
* corrupted or protected by
* having false line length
* values.
*
DEF UNFIX
AORG >2500
UNFIX LWPI USRWS
MOV @>8330,R1
MOV @>8332,R2
C R1,R2
JHE FIN
*
INC R2
S R1,R2
SRL R2,1
CI R2,BUFMAX
JGT FIN
*
SRL R2,1
MOV R2,@BUFLEN
INCT R1
LI R4,BUFF
*
LOOP MOVB *R1+,*R4+
MOVB *R1+,*R4
DEC R4
DEC *R4
INCT R4
INCT R1
DEC R2
JNE LOOP
LI R5,>FFE8
AGAIN MOV @BUFLEN,R3
LI R2,ZER0
LI R1,BUFF
DECT R1
*
NEXT INCT R1
C *R1,*R2
JL SKIP
MOV R1,R2
SKIP DEC R3
JNE NEXT
*
MOV *R2,R6
MOV *R1,*R2
S R6,R5
DEC R5
SWPB R5
MOVB R5,*R6
MOV R6,R5
DEC @BUFLEN
JNE AGAIN
*
FIN LWPI >83E0
CLR R0
MOVB R0,@>837C
RT
*
USRWS BSS 32
BUFLEN BSS 2
ZERO DATA >0000
BUFMAX EQU >1800
BUFF BSS BUFMAX
*
END
Load that offensive Basic program that causes your computer to lock-up when you try to list it. Then type CALL INIT :: CALL LOAD("DSK1.OBJECT") [ENTER]
Next execute the machine code routine by typing
CALL LINK("UNFIX") [ENTER]
When the cursor re-appears on the screen you will be able to LIST or edit the program.
Check the start of the program to see if those few lines listed earlier are still there.
If so, then delete these lines before you re-save the program otherwise it will reset line length values each
time you run the program.
A great deal faster! This machine code is for loading with ExBas ONLY! Why do we need to have the length right for editting? 'Cos if the length byte is 255 bytes, when you delete (or edit) the lines, the computer will delete 255 bytes, and if the line is shorter, you are going to lose other data, probably partial lines, which will be very sad!
Review: Tris module
MODULE REVIEW: TRIS- Famous Game! Asgard Software, 1939. Main author Jim Reiswho cannot know this game? The TI module is a perfectly good emulation, in which tetromino shapes fall, can be rotated and dropped, and must be formed into a solid horizontal line. You score by how quickly you line the shapes up and drop them into place. Game ends when the shapes stack up to the top due to your having left empty spaces in horizontal lines. This is very similar to the Hulpke disk version, except that you may not amend the "next shape" (which is optionally displayed in the module version) and the module version benefits by automatically increasing in speed as play progresses- Hulpkes version plays constantly at the same level.
A good module for unexpanded owners who cannot play the Hulpke disk version, this is also a good module ior all games players Music and sound are credited to Ken Gilliland, Bruce Harrison, Jim Reiss. HOW GOOD IS IT? My wife -Cathy- has not played a module game before- she is hooked on this one, belting the living daylights out of a joystick and not infrequent *expletive deleted*s! My six year old doesn't get too high a score at the easiest level but still likes a go. I play it. Look- if you ever play games this is one tor you. If you have never played a game on your TI, this is still one ior you. Buy it. OK!
Recommended
Review- Disk- Balloon Wars
GAME REVIEW- DISK- BALLOON WARS- 1985. ASGARD SOFTWARE Written by John Morrison.Quite an old game this one, I've seen it advertised but not reviewed. Its an ExBas game, but uses disk: data files, so is not suitable for tape.
My disk was quite unusual, having a disk jacket a trifle floppier than the disk inside it. I was surprised when my drive read it (and copied it onto a more substantial disk!). The program is list protected but most disk owners know what to do about that!
Your task is to pilot a hot air balloon from screen left to right across several screens, using fuel as you go! There are enemy troops below with a nasty habit of firing at you- you may avoid their shots and you may bomb them. On some screens, after removing the enemy, you may land for repairs and restocking.
The documentation is in error- it is joystick down to release a bomb, and joystick up to drop a sandbag (not vice versa).
This program is not exactly sophisticated., and the graphics are very simple, but it is an interesting game which presents some simple strategic decisions to be made. If you like a game to can get into quickly, you'll like this one.
Review- Disk- TI Base Vn 3
UTILITY REVIEW- TI BASE VERSION THREE- DISK. TEXAMENTS. US$25+ $9 p and p.We have already covered earlier versions, this one is fully compatible with earlier one but spreads its wings in many new directions!
Of particular interest is the ability to place command files into VDP memory them as memory images and save and load them as memory images - for really rapid operation, more so if you are using a ram disk for the actual data! There is also the availability of using this option to create macros- making up your own commands from the ones supplied.
The report generator is possibly misnamed, it is a database of command files, and while it can certainly be used to produce screen and printed formats, it is not limited to that use. The major limit would be the number of commands you can fit into the database, but with the macro facility already indicated above, this additional facility gives the programmer considerable power to hide TI Base behind a fast and friendly user interface- the user need never know TI base is in use, apart from the loading screen!
Inverse characters are available, but the documentation is incomplete. You can turn all text inverse with the command SET INVERSE ON but you may also mix normal and inverse text by leaving SET INVERSE OFF and inserting characters with ASCII codes 128 higher than usua1 - eg an inverse A is character 193 instead of 65. These characters are used on Epson printers as the italic set. You cannot enter a character 193 into a command fle using TI Writer, you must use the TI Base editor which has another new option, familiar to PC users as the ALT key: hold down CTRL and key in the three numbers of the character you want (eg 193) and that character will appear on screen.
(As the TI Base editor is limited to small command files, we have in the disk library a utility to merge such command files into longer ones). Of course, as a program/language becomes more powerfu1 it tends to become harder to use, and indeed, to become underused as few bother, but TI Base can be used without command fi1es at all, for the early owner, leading upwards to a very professional database presentation for the more experienced programmer who wishes to impress (very often it's the experienced programmers who leave the stitches showing!).
If you want a database, this is the one! Can work with one SSSD disk drive, works better with two disk drives, and is happy with ram disks or hard drives.
Graphics for The Missing Link
 An issue of Rambles without fractal programs would be amiss, so here are are some fractal programs for you.
An issue of Rambles without fractal programs would be amiss, so here are are some fractal programs for you.
There is a program which gives an audio representation of bifurcation.
Then we have a program which draws the little character alongside - take a look at him and work out a program to draw him! Can't do it? Look at the listing. Odd! Variables X & Y can take almost any value to start - high initial values mean you need a lower multiplier for A & B.
And finally, a program that draws wallpaper, composed entirely of circles- start with a SIDE of say 20 and gradually work up to say 2000. The pattern will recede and different detail will become apparent.
Bifurcated graphics realised as sounds
From an article BIFURCATED SOUNDS by Leon Heller in Issue 10 of FRACTAL REPORT. Based on a book by Becker and Dorfler regarding presentation of values generated by a Feigenbaun type system... what the heck, a DIFFERENT way of producing random sequences of tunes instead of cycling round CALL SOUND(-100,1l0+RND*1000,4)100 ON WARNING STOP
120 RANDOMIZE
140 CALL CLEAR :: PRINT "ANY KEY FOR NEW PATTERN" : :
160 X=RND :: PRINT "X =";X
180 R=3.2+RND :: PRINT "G FACT =";R: "IF >3.57 PATTERN IS CHAOTIC"
200 FT=1000
220 FB=111
240 EF=360+230*RND
260 PRINT "EF= ";EF
280 D=70+RND*100
300 PRINT
320 X=R*X*(1-X) :: N=EF*X :: IF N>550 OR N<56 THEN 140 ELSE CALL SOUND(-D,N*2,6*RND)
340 CALL KEY(0,A,B) :: IF B=1 THEN 140 ELSE 320
360 END
Also from Issue 10 of Fractal Report, by Tom Marlow, based on R Denaney, this requires THE MISSING LINK as it stands but readily converted to any utillity allowing bit map graphics
90 ! GINGERBREAD MAN 1 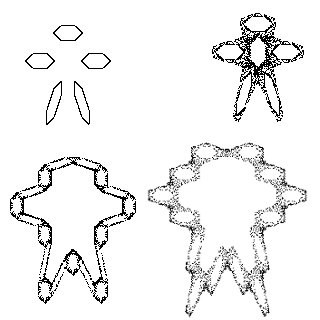
100 CALL LINK("CLEAR")
110 ! H=240 :: V=180
120 X=8.56
130 Y=3.76
140 FOR L=1 TO 5000
150 NX=1-Y+ABS(X):: NY=X :: X=NX :: Y=NY
160 A=100+X*8-Y*8
170 B=70+X*8+Y*8
180 CALL LINK("PIXEL",A,B)
190 NEXT L
200 CALL LINK("PRINT",180,180,"END")
210 GOTO 210
OR TRY:
90 ! GINGERBREAD MAN 2
100 CALL LINK("CLEAR")
110 ! H=240 :: V=180
120 X=9*RND
130 Y=X+2*RND-2*RND
140 FOR L=1 TO 3300
150 NX=1-Y+ABS(X):: NY=X :: X=NX :: Y=NY
160 A=100+X*7-Y*7
170 B=70+X*7+Y*7
180 CALL LINK("PIXEL",A,B)
190 NEXT L
200 CALL LINK("PRINT",180,180,"END")
210 GOTO 210
ALSO
90 ! GINGERBREAD MAN 3
100 CALL LINK("CLEAR")
140 X= -0.100000000001 ! needs the 10x 0's and final 1!
150 Y=0
180 FOR L=1 T0 5299
190 NX=1-Y+ABS(X):: NY=X :: X=NX :: Y=NY
200 A=100+X*14-Y*14
210 B=60+X*14+Y*14
220 CALL LINK("PIXEL",A,B)
230 NEXT L
240 CALL LINK("PRlNT",180,180,"END")
260 GOTO 260
And finally a little wallpaper
100 REM CIRCLES
110 REM JE CONNETT/PWH MOON/S SHAW 1990
120 SIDE=20 ! anything from 10 to 2000 but avoid multiples of 150
130 REM
140 CALL LINK("CLEAR")
150 FOR I=l TO 150 :: FOR J=1 T0 150
160 X=I*SIDE/150 :: Y=J*SIDE/150 :: C=INT(X*X+Y*Y) :: D=C/2 :: IF D-INT(D)>0.1 THEN 180
170 CALL LINK("PIXEL",I+20,J+20)
180 NEXT J :: NEXT I
190 PIC=PIC+1 :: A$="DSK2."&STR$(PIC)
199 REM OMIT LINE 200 IF YOU DON'T WANT TO SAVE
200 CALL LINK("SAVEP",A$)
210 SIDE=SIDE*1.2 :: GOTO 140
220 END
Go to top of page